Rapid7 Metasploit
UK
The table below provides summary statistics for permanent job vacancies requiring Metasploit skills. It includes a benchmarking guide to the annual salaries offered in vacancies that cited Metasploit over the 6 months leading up to 30 April 2025, comparing them to the same period in the previous two years.
| 6 months to 30 Apr 2025 |
Same period 2024 | Same period 2023 | |
|---|---|---|---|
| Rank | 672 | 832 | 963 |
| Rank change year-on-year | +160 | +131 | +232 |
| Permanent jobs citing Metasploit | 12 | 53 | 24 |
| As % of all permanent jobs advertised in the UK | 0.023% | 0.054% | 0.023% |
| As % of the Development Applications category | 0.22% | 0.55% | 0.16% |
| Number of salaries quoted | 6 | 46 | 12 |
| 10th Percentile | £41,000 | £62,500 | £47,375 |
| 25th Percentile | £49,625 | £67,500 | £57,500 |
| Median annual salary (50th Percentile) | £67,500 | £75,000 | £90,000 |
| Median % change year-on-year | -10.00% | -16.67% | +44.00% |
| 75th Percentile | £89,688 | £82,500 | £98,000 |
| 90th Percentile | £95,000 | £120,000 | - |
| UK excluding London median annual salary | £67,500 | £53,750 | £52,500 |
| % change year-on-year | +25.58% | +2.38% | +45.83% |
All Development Application Skills
UK
Metasploit falls under the Development Applications category. For comparison with the information above, the following table provides summary statistics for all permanent job vacancies requiring development application skills.
| Permanent vacancies with a requirement for development application skills | 5,498 | 9,566 | 15,038 |
| As % of all permanent jobs advertised in the UK | 10.54% | 9.73% | 14.46% |
| Number of salaries quoted | 3,807 | 6,755 | 9,183 |
| 10th Percentile | £37,574 | £36,250 | £41,250 |
| 25th Percentile | £46,250 | £45,000 | £50,000 |
| Median annual salary (50th Percentile) | £60,000 | £60,000 | £65,000 |
| Median % change year-on-year | - | -7.69% | +4.00% |
| 75th Percentile | £75,000 | £77,500 | £83,750 |
| 90th Percentile | £96,750 | £95,000 | £100,000 |
| UK excluding London median annual salary | £57,500 | £55,000 | £57,500 |
| % change year-on-year | +4.55% | -4.35% | +4.55% |
Metasploit
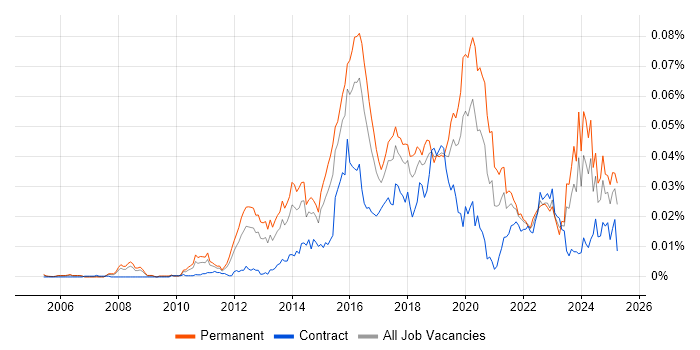
Job Vacancy Trend
Job postings citing Metasploit as a proportion of all IT jobs advertised.
Metasploit
Salary Trend
3-month moving average salary quoted in jobs citing Metasploit.
Metasploit
Salary Histogram
Salary distribution for jobs citing Metasploit over the 6 months to 30 April 2025.
Metasploit
Top 8 Job Locations
The table below looks at the demand and provides a guide to the median salaries quoted in IT jobs citing Metasploit within the UK over the 6 months to 30 April 2025. The 'Rank Change' column provides an indication of the change in demand within each location based on the same 6 month period last year.
| Location | Rank Change on Same Period Last Year |
Matching Permanent IT Job Ads |
Median Salary Past 6 Months |
Median Salary % Change on Same Period Last Year |
Live Jobs |
|---|---|---|---|---|---|
| UK excluding London | +204 | 8 | £67,500 | +25.58% | 4 |
| England | +146 | 8 | £67,500 | -10.00% | 5 |
| London | +66 | 4 | £90,000 | +20.00% | 4 |
| Work from Home | +165 | 3 | £90,000 | +20.00% | 9 |
| Northern Ireland | +37 | 3 | - | - | 2 |
| South West | +113 | 2 | £67,500 | - | 1 |
| South East | - | 2 | - | - | 1 |
| Scotland | - | 1 | £37,500 | - |
Metasploit
Co-occurring Skills and Capabilities by Category
The follow tables expand on the table above by listing co-occurrences grouped by category. The same employment type, locality and period is covered with up to 20 co-occurrences shown in each of the following categories:
